In a world increasingly plagued by cyber scams, iCloud phishing attempts have become particularly sophisticated, employing urgent and alarming messaging to deceive unsuspecting users. Recently, reports have surfaced regarding fraudulent emails claiming to be from Apple, concerning issues related to iCloud storage. These scams not only target individuals through manufactured personal threats but also aim to gather sensitive information. Understanding how to recognize and protect against such scams is crucial to maintaining online security.
| Article Subheadings |
|---|
| 1) The Anatomy of iCloud Scams |
| 2) How to Identify iCloud Scams |
| 3) Steps to Protect Yourself |
| 4) What to Do If You’ve Been Scammed |
| 5) Kurt’s Key Takeaways |
The Anatomy of iCloud Scams
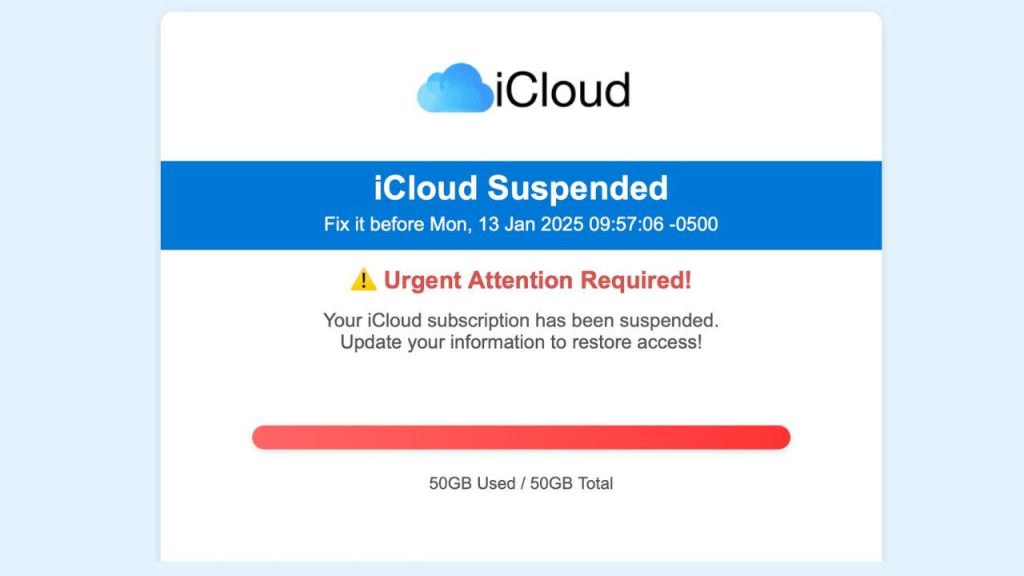
iCloud scams have developed a specific pattern designed to evoke urgency and fear. A recent example involved two emails that alarmed recipients with titles such as “Payment Failure for iCloud Storage Renewal” and “iCloud Suspended. Fix it before Mon, 13 January 2025.” In both instances, the emails exhibited typical phishing traits, including alarming language, threats of account suspension, demands for payment information updates, and links directing users to unverified websites.
These emails are crafted to closely resemble authentic communications from Apple, even employing similar styles and branding. However, key red flags indicate their fraudulent nature. Recipients should remain vigilant against such tactics, as the stakes involve users’ personal and financial information potentially falling into the hands of cybercriminals.
How to Identify iCloud Scams
To safeguard against these scams, users should be aware of notable signs indicative of fraudulent emails:
- Check the sender’s email address: Legitimate communication from Apple originates from “@apple.com” or “@icloud.com” domains. Scammers often use similar but distinctly different emails.
- Look for spelling and grammatical errors: Authentic communications are free from significant mistakes, whereas scam emails often contain glaring errors.
- Be wary of urgent deadlines: Scammers often employ artificial deadlines to apply pressure, urging quick action without careful consideration.
- Verify account details: Ensure that any account information mentioned matches what is known. Mismatches can indicate a scam.
- Hover over links without clicking: This allows a preview of the URL destination, helping to verify legitimacy. Often, scam URLs will not reflect official Apple domains.
These precautionary methods are essential to discerning genuine Apple communications from deceptive messages. Cybersecurity awareness and critical thinking can act as initial layers of defense against falling victim to such threats.
Steps to Protect Yourself
Upon receiving a suspicious email that appears to be from Apple or iCloud, it is vital to follow several protective steps:
- Don’t click any links or download attachments: Engaging with these could lead to phishing websites or the installation of malware on your device.
- Use strong antivirus software: Implement reputable antivirus software across all devices to help shield against malicious attacks. This software can also alert users to threats posed by phishing emails.
- Check your account directly: Rather than utilizing links provided in the email, navigate directly to appleid.apple.com or the device’s settings for confirmations.
- Update your Apple ID password: If there is any indication that your account may have been compromised, changing the password is immediate necessity.
- Enable two-factor authentication (2FA): This adds an additional strong layer of protection to your Apple ID.
- Report the phishing attempt: Forward suspicious emails to reportphishing@apple.com.
Employing these strategies significantly enhances personal online security and reduces vulnerability to cyber scams.
What to Do If You’ve Been Scammed
If you fear that you might have succumbed to an iCloud scam, immediate action is necessary:
1) Change your Apple ID password immediately: Ensure that you create a robust, unique password that hasn’t been utilized elsewhere.
2) Check for unauthorized changes: Log in to your account at account.apple.com to inspect for unfamiliar devices or payment information.
3) Contact Apple Support: Reach out through official channels for assistance and forward the suspicious email to reportphishing@apple.com.
4) Monitor your financial accounts: If personal data was potentially compromised, keep a close eye on financial transactions for unwarranted activity.
5) Consider placing a fraud alert: Contact credit reporting agencies and the relevant authorities to take preventive measures.
6) Utilize identity theft protection services: Such services can monitor personal information and provide alerts regarding any potential misuse.
These actions can help mitigate the damage caused by a scam and assist in preventing future occurrences.
Kurt’s Key Takeaways
It is crucial to remember that Apple will never ask for sensitive information, passwords, or security codes via email or text. When unsure about the authenticity of any communication from Apple, it is always safest to err on the side of caution. Contacting Apple directly through their official channels is advisable.
By remaining aware and following established guidelines, individuals can effectively protect themselves from iCloud scams, thus safeguarding their personal information. Taking a moment to verify messages can lead to enhanced safety online.
| No. | Key Points |
|---|---|
| 1 | iCloud scams exhibit urgent messages designed to scare users into action. |
| 2 | Detect scams by verifying email sender addresses and being wary of urgent language. |
| 3 | Engage antivirus software and practice caution with links in suspicious emails. |
| 4 | Monitoring accounts and taking prompt action is key if scammed. |
| 5 | Directly contact Apple for support during suspicious activity. |
Summary
The rise of iCloud scams underscores the necessity for heightened vigilance and awareness among users. Recognizing the tactics used by scammers is vital in maintaining not only personal security but also the integrity of sensitive information. By following established guidelines and remaining cautious, users can better protect themselves against the ever-evolving landscape of cyber threats.
Frequently Asked Questions
Question: What should I do if I received a suspicious email about my iCloud account?
If you receive an alarming email, refrain from clicking any links or downloading attachments and verify the sender’s address. It’s best to check your account directly through the Apple website.
Question: How can I enhance my security on iCloud?
You can improve security by enabling two-factor authentication, using strong and unique passwords, and regularly monitoring your account for any unauthorized access.
Question: What characteristics should I look for in phishing emails?
Phishing emails often use urgent language, poor grammar, unfamiliar email addresses, and invasive requests for personal information. Be on alert for these signs to avoid falling victim.