Phishing attacks continue to pose a significant threat to internet users, evolving with technology and becoming increasingly sophisticated. A new phishing kit named Astaroth is gaining notoriety for its ability to bypass two-factor authentication (2FA) through advanced techniques such as real-time credential interception and session hijacking. This article explores the mechanics of Astaroth, its advanced features, the signs of infection, and practical steps users can take to protect themselves.
| Article Subheadings |
|---|
| 1) Understanding Astaroth: The New Face of Phishing |
| 2) The Mechanics Behind Astaroth’s Functionality |
| 3) Astaroth’s Advanced Features and Distribution |
| 4) Identifying Signs of Astaroth Infection |
| 5) Protecting Yourself Against Astaroth Phishing Attacks |
Understanding Astaroth: The New Face of Phishing
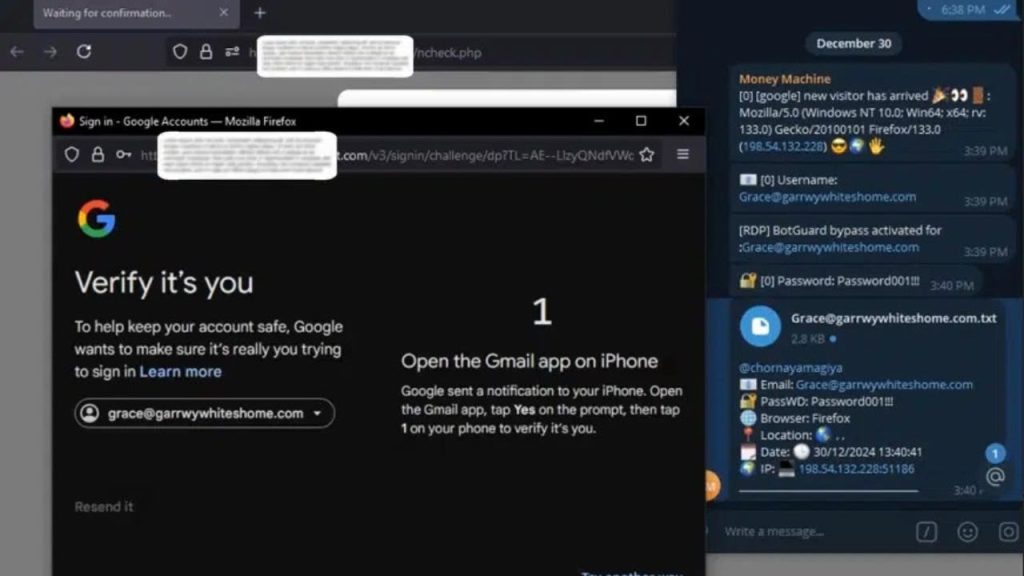
The digital landscape is continuously marred by phishing attacks, with Astaroth emerging as a pivotal threat in the realm of cybercrime. This phishing kit’s capability to effectively bypass traditional defense mechanisms such as two-factor authentication (2FA) places it among the most sophisticated tools utilized by cybercriminals today. Astaroth, in particular, is engineered to target popular authentication systems employed by services like Gmail, Yahoo, and Microsoft, undermining users’ sense of security.
The versatility of Astaroth lies in its ability to operate in real-time, allowing attackers to intercept and manipulate data exchanged between users and genuine online services. Reports indicate that Astaroth is infecting systems through deceptive links that resemble legitimate sites, enabling cybercriminals to execute their plans with alarming effectiveness.
This article aims to not only dissect the alarming mechanics of the Astaroth phishing kit but also to furnish users with essential knowledge to bolster their defenses against such vulnerabilities in cyberspace.
The Mechanics Behind Astaroth’s Functionality
At its core, Astaroth operates as a middleman, intercepting communication between unsuspecting users and genuine authentication services. The attack mechanism is activated when a user is tricked into clicking a malignant link, leading them to a website that is a near-perfect imitation of the intended legitimate site. These fraudulent sites benefit from valid SSL certificates, disabling typical security warnings and thus preventing red flags from alerting the user.
Once a user inputs their login credentials, including their username, password, and device information, Astaroth stealthily captures this crucial data before relaying it to the authentic site. What distinguishes Astaroth from traditional phishing techniques is its handling of two-factor authentication credentials. As soon as a user enters their temporary password or code—be it from an app, SMS, or push notification—Astaroth seizes this information and relays it directly to the attacker in real-time. This immediate transmission means that attackers can utilize the stolen codes before they even expire.
Additionally, Astaroth is adept at stealing session cookies, the small files that keep users logged into their accounts. By manipulating these cookies, cybercriminals can gain access to accounts without needing the user’s credentials or any secondary authentication, rendering conventional safety measures ineffective.
Astaroth’s Advanced Features and Distribution
What sets Astaroth apart from its competitors is not only its sophisticated interception capabilities but also its sustainability. Cybersecurity firm SlashNext has noted the kit’s resistance to traditional takedown efforts, as it employs bulletproof hosting to maintain its website’s functionality and reach. Attackers utilizing Astaroth benefit from continuous updates, ensuring that they can circumvent security patches implemented by IT teams globally.
For aspiring cybercriminals seeking to invest in Astaroth, it is advertised through underground cybercrime forums and platforms like Telegram. Priced at approximately $2,000 for six months of updates, the kit reflects a structured approach to cybersecurity in the cybercriminal world, where even malware becomes a commercially available product. There are even provisions for potential buyers to test the tool beforehand, enhancing its appeal.
Without a doubt, the ease of access and sophisticated features of Astaroth have contributed to its popularity among cybercriminals, leaving ordinary users vulnerable to exploitative attacks.
Identifying Signs of Astaroth Infection
Recognizing the signs of an Astaroth infection is crucial for users who want to mitigate its effects. Several indicators may hint at previous or ongoing invasions:
- Unexpected Account Logins or Security Alerts: If you receive warnings from Gmail or other services about logins from unknown locations or devices, it could indicate unauthorized access.
- Mysterious Account Logouts: If an attacker executed a session hijack, you may find yourself inexplicably logged out of your accounts.
- Unsolicited Password Changes: Alterations to your recovery details or passwords without your consent suggest malicious interference.
- System Performance Issues: Astaroth may employ normal Windows processes to operate quietly. If your system runs slower or displays strange Task Manager activity, take note.
- Bizarre Browser Behaviors: Issues like incorrect data auto-filling or frequent errors could result from an infection.
- Unfamiliar Programs Running: Any suspicious applications or scripts in the background should be investigated, especially if they exhibit unusual network activity.
Protecting Yourself Against Astaroth Phishing Attacks
Taking preventive measures to stay safe from Astaroth phishing attacks is the responsibility of all users. Here are several practical steps that can significantly enhance security:
- Avoid Unknown Links: Most phishing attacks, including Astaroth, hinge on user interaction. Exercising caution when clicking links can prevent exposure to malwares.
- Double-Check Website URLs: Before entering sensitive information, ensure you are accessing the authenticated website. Bookmarks for trusted sites can significantly reduce risk.
- Keep Devices Updated: Regularly updating your operating system and applications can help close potential pathways malware utilizes to attack.
- Utilize Alternative Authentication Methods: Reducing reliance on traditional passwords can minimize the risk of credential theft. Opt for methods such as Google Sign-In or Apple Sign-In.
| No. | Key Points |
|---|---|
| 1 | Astaroth is a sophisticated phishing kit that bypasses two-factor authentication. |
| 2 | The kit operates as a middleman, capturing credentials in real-time. |
| 3 | It is marketed through underground forums and boasts a subscription model for updates. |
| 4 | Users should watch for signs like unexpected logins and slow system performance. |
| 5 | Preventive measures include avoiding unknown links and keeping software updated. |
Summary
The emergence of the Astaroth phishing kit exemplifies the evolving nature of cyber threats, bypassing traditional security measures and posing substantial risks to personal and organizational data. The combination of real-time credential interception and session hijacking allows attackers unprecedented access to sensitive accounts, demonstrating the need for enhanced vigilance among internet users. By understanding the mechanisms behind Astaroth and adopting robust protective measures, individuals can significantly minimize their risk of falling victim to such advanced cyber threats.
Frequently Asked Questions
Question: What is a phishing kit?
A phishing kit is a collection of tools and resources used by cybercriminals to create and execute phishing attacks. These kits allow attackers to mimic legitimate websites and capture user credentials without their knowledge.
Question: How can I tell if I’ve been phished?
Signs of phishing include unexpected account logins, unauthorized transactions, and receiving alerts for changes you did not initiate. If you suspect you have been targeted, it’s crucial to change your passwords immediately and monitor for unusual activity.
Question: Is two-factor authentication enough to protect me?
While two-factor authentication adds an additional layer of security, it is not foolproof. Advanced phishing methods, like those employed by Astaroth, can bypass 2FA. Therefore, users should also adopt comprehensive protection measures such as using strong passwords and security practices.